Phishing and scam attacks are higher than they’ve ever been. Phishing attempts typically try to scare you into clicking on links, opening attachments, and/or open a Google form and provide information. Any company you do business with should already have the information being requested. TDS will never contact you directly and ask you to verify any part of your account. In fact, if you want to make any changes to your account, we require you to verify that you’re authorized to do so.
If you receive a phishing email to your TDS.net account which claims to come from TDS, please attach the suspicious email to a new email (right click the email and select forward as an attachment) and send to abuse@tds.net. This will give our team all necessary information so we can act. Then immediately delete the email.
DO NOT:
- Respond to the email in any way.
- Click on any links.
- Open any attachments.
- Provide any data to websites mentioned.
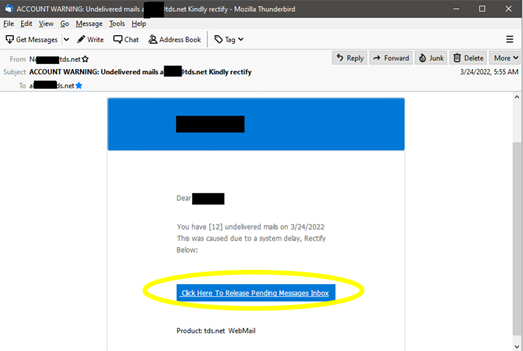
Below are a few real-life examples our TDS customers have received and since most phishing emails have some common elements, we’ve listed how to spot the common errors.
- Look at the sender’s email address. Often this is your first clue something is amiss—if the address doesn’t match the business supposedly sending the email, it’s probably a scam.
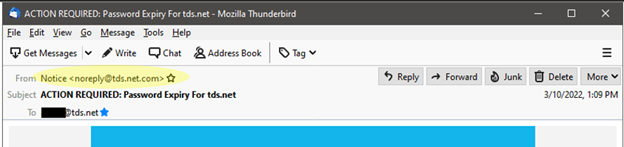
- Look for spelling and grammar mistakes. Frequently cybercriminals make some obvious grammar errors. Sure, mistakes happen even in professional communications, but they’re rare. If you notice errors, you should be on high alert.
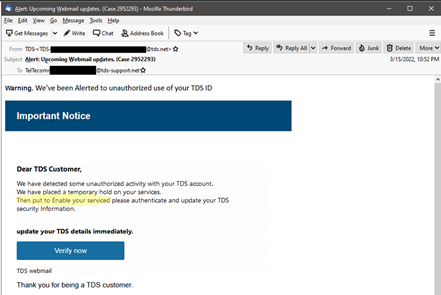
- Don’t fall for threats. Watch for phrases such as “your account will be closed” or “your account has been compromised.” If TDS does contact you about a vulnerable or compromised account, you will never be asked to click a link and you will always receive a ticket number and can call the help desk with that number to confirm authenticity.
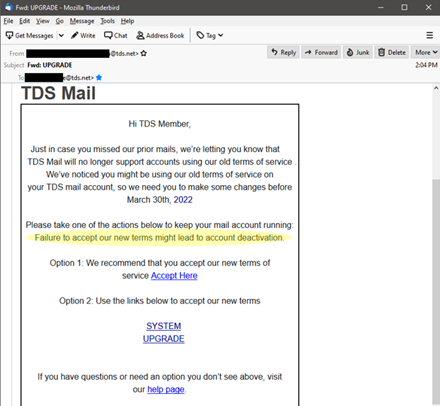
- A company you do business with is asking for information. It’s easier to scam people when they think the email is from a company they already know—just remember the company probably already has (or should have) the information being requested.
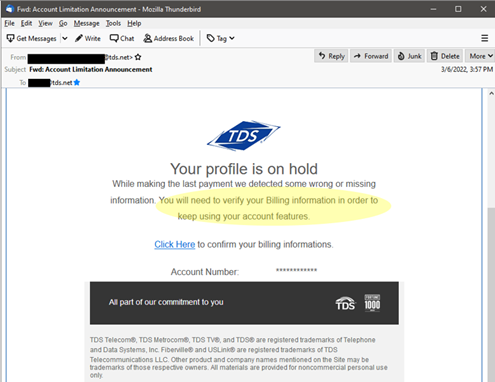
- Beware of links. Always have a healthy dose of suspicion if the email demands you to take action by clicking. You can use your mouse to hover over any links in an email to reveal the web address but know this too can be faked. Clear signs of fakery include: the address is a cryptic set of numbers, looks nothing like the web address from the supposed sender, or is an .exe file (which could actually be malicious software).
Report all other phishing and scam emails to the Federal Trade Commission at ReportFraud.ftc.gov and forward it to the Anti-Phishing Working Group at reportphishing@apwg.org. (If scammers contact you by text message or phone, report that, too.) We also have a how-to guide to help if you think you’ve been a victim of a data breach.
If you’ve ever wondered how scammers even get your email address in the first place, here are some of the ways they do it (according to Microsoft, The Balance Everyday, and others):
- They use web crawlers that look for the @ symbol. Scammers have developed sophisticated automated tools that search the internet and gather email addresses. These can be found in insecure files, blog comments, winner lists, or even on social media profiles.
- They guess. Scammers will gather lists of common names and words, and combine them with popular email address services/internet service providers and just try and see if it works. Again, scammers are using tools to do this by the thousands.
- They buy lists. Read the privacy policy on any website before handing of your email—the company may be able to legally sell your information, including your email address. On the dark web, there are also illegal lists available to purchase.
- Hacking. Cybercriminals are not above hacking into databases to get email addresses. They can use them, or they can sell what they find—or both.
- Fake websites. Fake sweepstakes are a classic method for getting people to readily give away their information. Always double check that it’s legitimate by checking out the company tied to the offer, and looking out for misspellings, bad grammar, and vague details.


